SIEM In Azure
What is Azure Sentinel?
In short, it is an easily scalable and cloud-native solution for threat detection and security analysis. It provides everything ranging from alerts, to proactive hunting, and threat responses.
Overview:
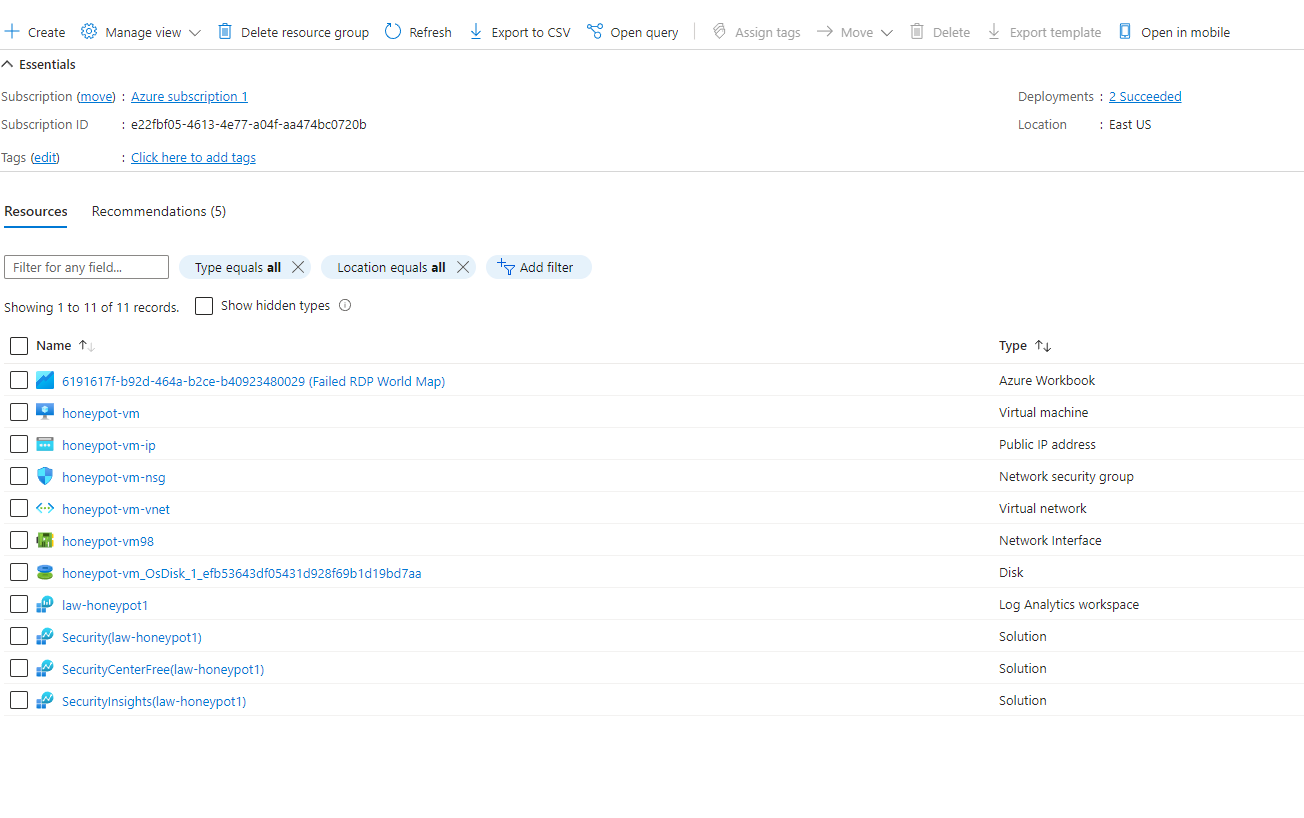
Creating an Azure Subscription, then creating a virtual machine in Azure. This virtual machine will have firewall and windows firewall off so that it is exposed to the internet and attackers. Then a log repository in Azure called Log analytics workspace will be created which will be used to ingest logs. Then Azure Sentinel will be set up to map all the different attacker data. PowerShell will also be used to extract windows IP addresses, send it to a 3rd party, then use that information to create a custom log with geographic data.
Preparation:
The first thing that needs to be done is to create a free Azure Account. You will have to enter a credit card for this, but you will get 200 dollars of free Azure credit that you can use for the lab and beyond. Be sure that once your done with lab, go to resource group and make sure everything is deleted.
The first thing to do is create a virtual machine. This is the machine that will be facing the web, and people from other countries will be trying to attack it.
Create a new resource group. Everything in this project will be associated with it. We will title it honeypot lab.
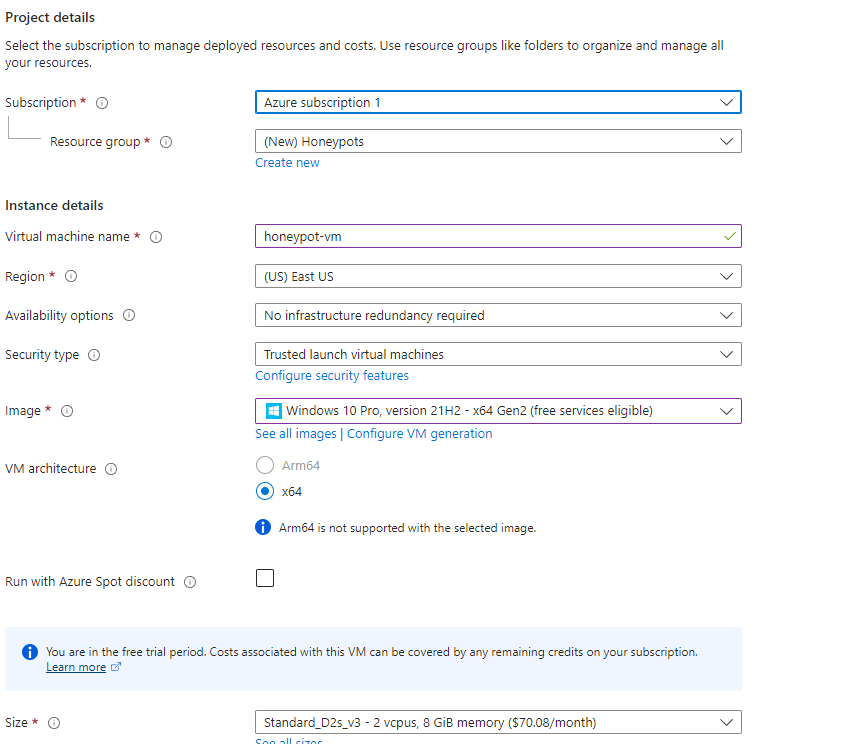
The username/password for the admin account isn't that important, but it should be saved somewhere. Everything else can be left default.
When you get to networking, go to advanced for NIC network security group. This is a network firewall.
Advanced > create new. Remove the default rule and allow everything into the VM. It will look like this.
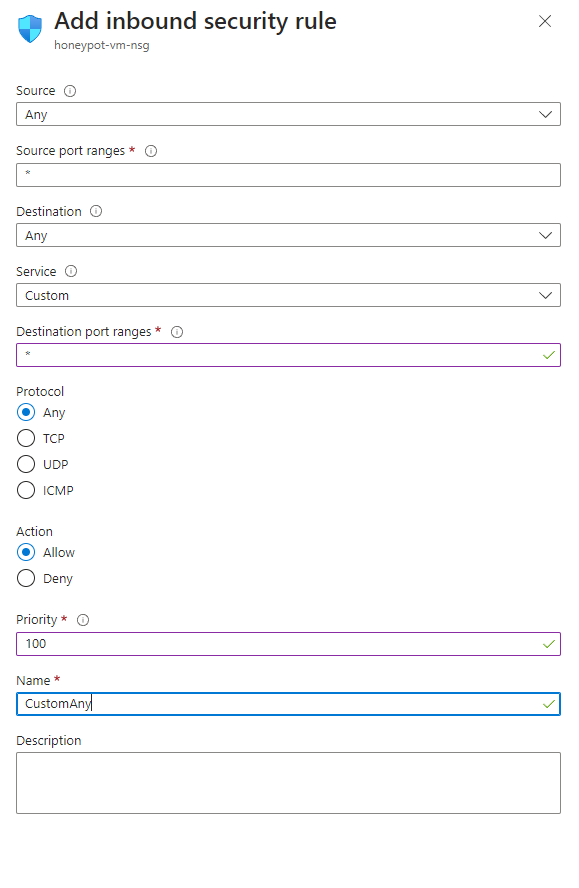
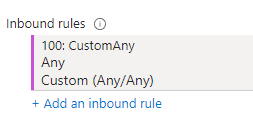
The point of this is to make the VM very discoverable quickly. Normally you wouldn't do this, however this is mainly to generate traffic.
The next step is to create a log analytics workspace. The purpose of this is to ingest logs from the virtual machine. We will ingest event logs and create our own custom log that contains geographic information so we can discover where attacks are coming from.
In the create log analytics workspace:

Next,we'll go to the security center and enable the ability to gather logs from thevirtual machine into the log analytics workspace. Go to Microsoft Defender ForCloud > Environment Settings and Defender Plans. Make sure SQL server is off and AzureDefender is on.
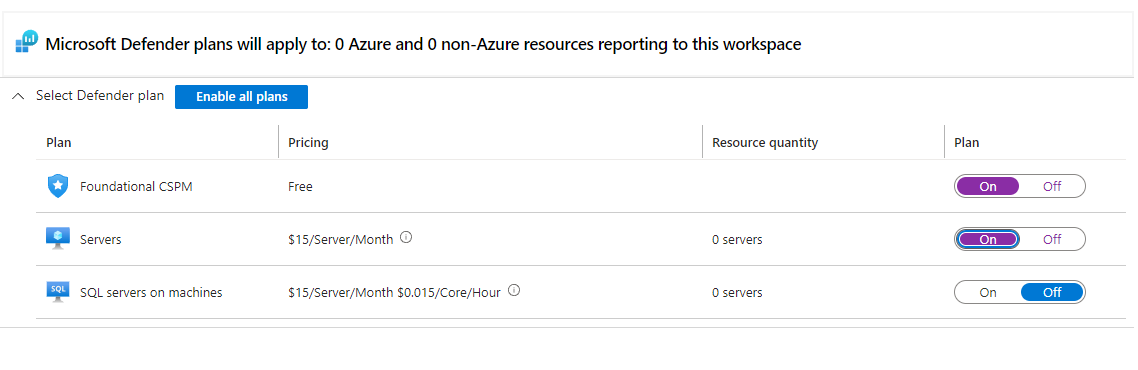
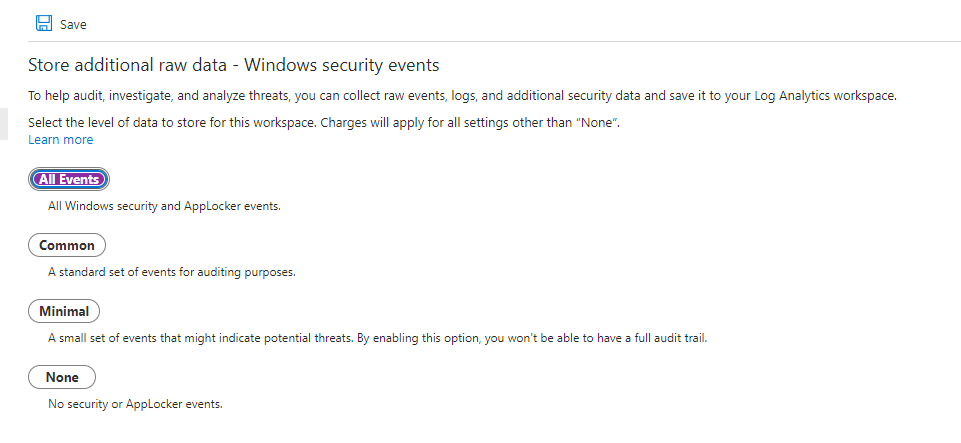
In data Collections, allow it to store all events.
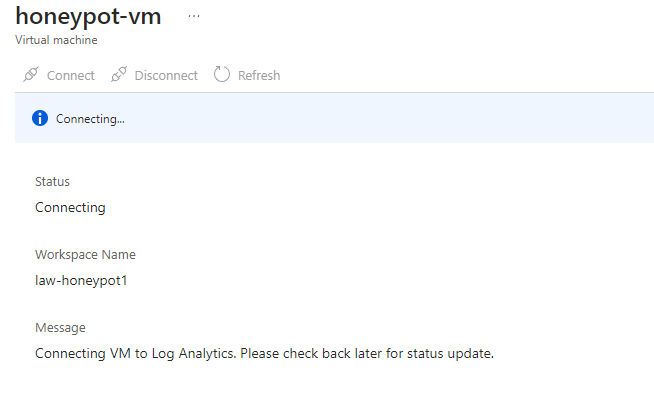
Go back to log analytics workspace and connect to the virtual machine.
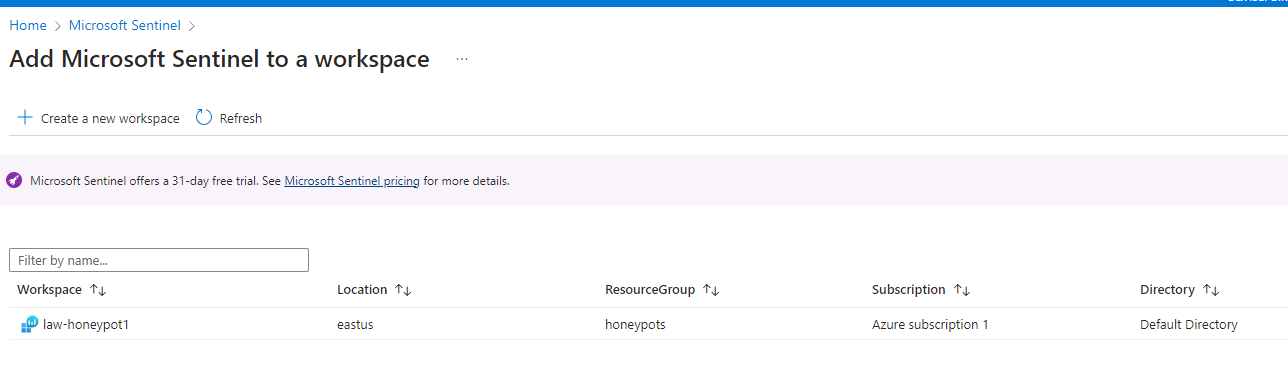
The next step is toset up Sentinel which is the SIEM we are using to analyze the attack data. Goto azure sentinel > create and pick your law-honeypot1.
Nowgo to the start menu and open up RDP on your windows.
You will have to click more choices and use the information that you made when initially creating the Virtual Machine. Say no to all the extra prompts. You can tell it’s a VM because of the IP at the top.
Now go to the Event Viewer.
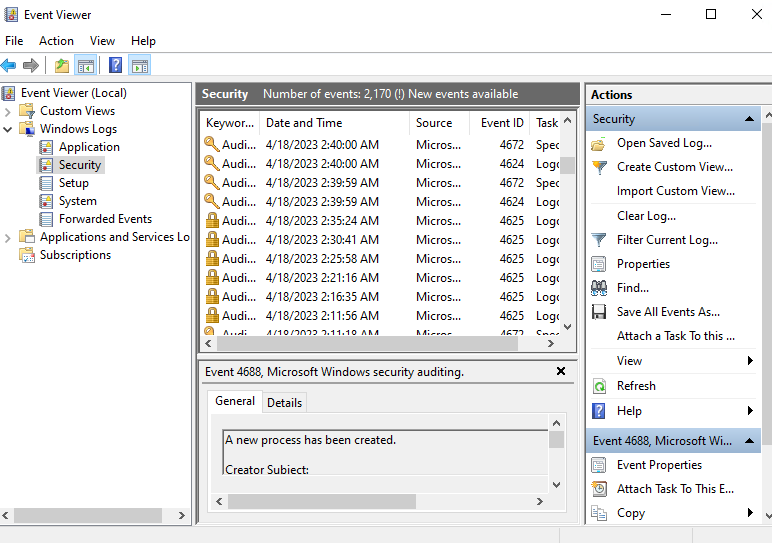
We will be focusing on EventID 4625. If you click into the events you will be able to see login fails and the IP address that it is coming from. What we will do is take the IP address, use an IP geolocation API. We will push the IP to the API and it will push the country, and where those login attempts are coming from. We will send those longs to azure, then use Sentinel to plot out the different attackers on the map.
On the VM to make sure that it is discoverable, we will turn off the firewall so that the VM is susceptible to ICMP attacks.
To demonstrate, first we will ping the public IP address of the VM and it won't give any response.
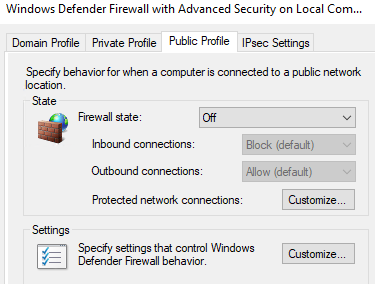
Go to wf.msc and turn all the firewall properties off. That would be domain profile, private profile, and public profile. Now when I try to ping the server from the command line, I can see ICMP requests.

Next, we will be using the Windows Log Exporter.ps1 and download it to the VM. All you have to do now is go to ipgeolocation.io and sign up. When you sign in you get a key and run the script. The log file gets exported to ProgramData. If there is no log file it will create a default log file.
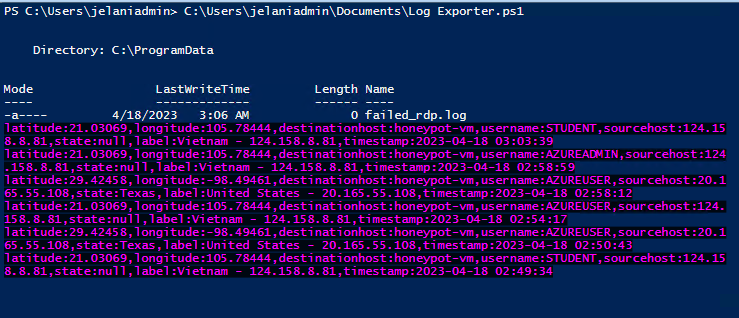
Now go into Azure and go to Log Analytics Workspace and go to Custom Logs. We will minimize the virtual machine and copy and paste the data into a notepad
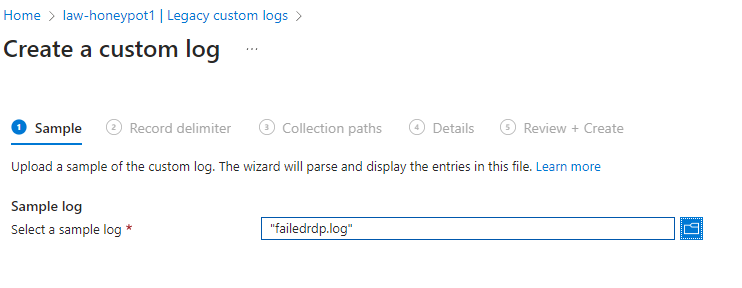
Clicknext and when they ask for the Path to the VM use the naming convention. Minewas: C:\ProgramData\failed_rdp.log
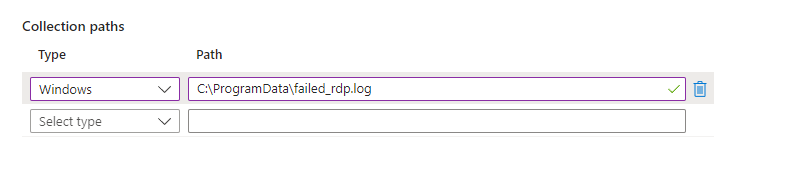
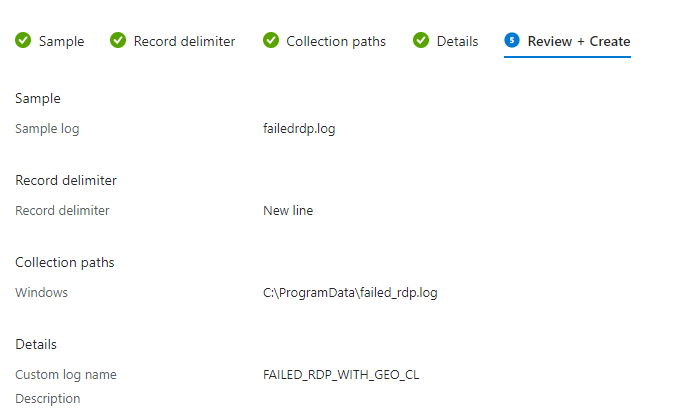
You’re going to have to wait 15 minutes to an hour for the Logs to be able to update and run the queries that you want.
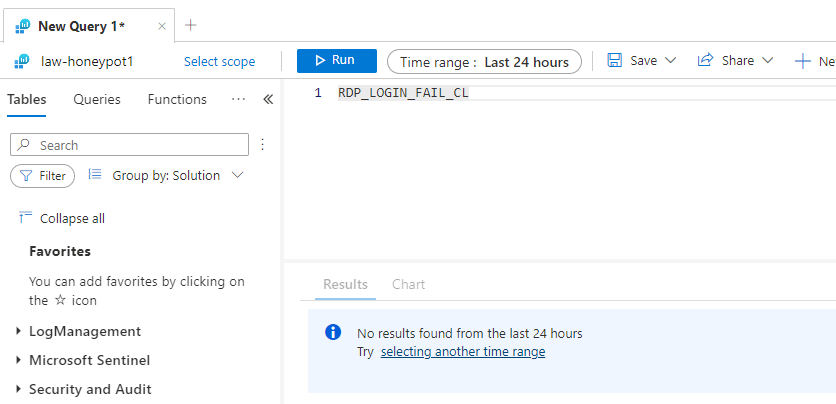
When the results are ready, is when you should move onto the next part.
Expand one of the logs and click the 3 dots to extract fields and see the RawData. In the RawData log you will be able to see latitude and longitude. Extract the fields by highlighting the portion that you need. Rename the Field Title accordingly
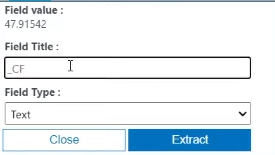
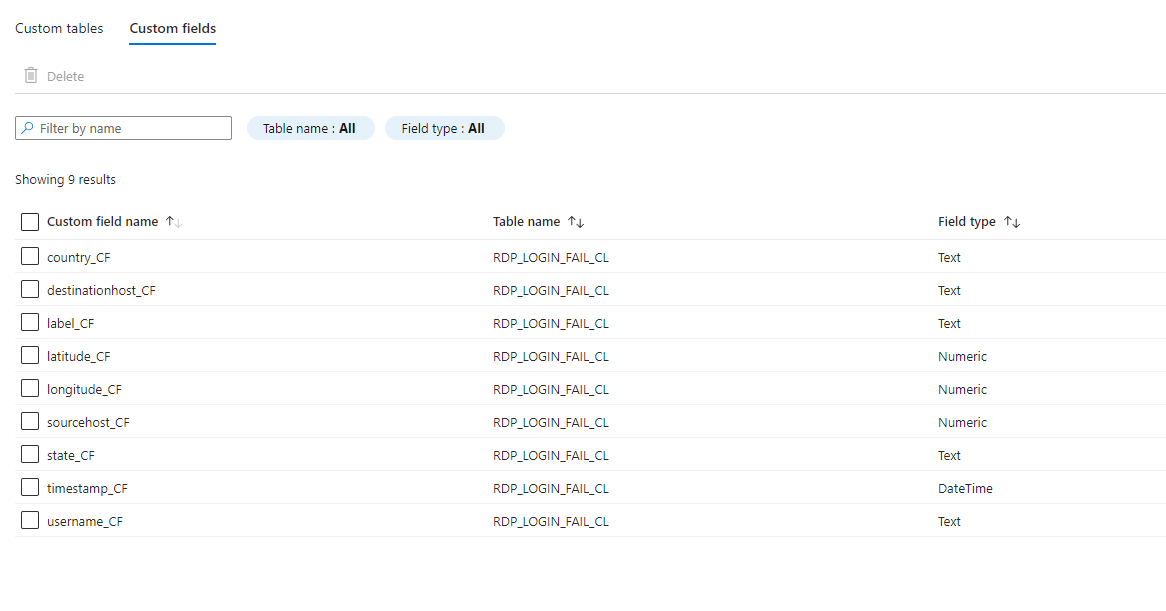
It should be latitude/numeric and longitude/numeric. You can also extract the country just in case. I also did an extraction for destination host, username, sourcehost, state, country, label, and timestamp. These can be found in custom fields.
The next step is towait for the bad people on the internet and while waiting for this, set up themap in Sentinel. Go to portal.azure.com and look up Sentinel.
Go to Workbook andadd a new one. Go to edit, remove the existing queries then add query.
Mine was as follows:
RDP_LOGIN_FAIL_CL | summarize event_count=count() by sourcehost_CF, latitude_CF, longitude_CF, country_CF, label_CF, destinationhost_CF
| where destinationhost_CF != "samplehost"
| where sourcehost_CF != ""

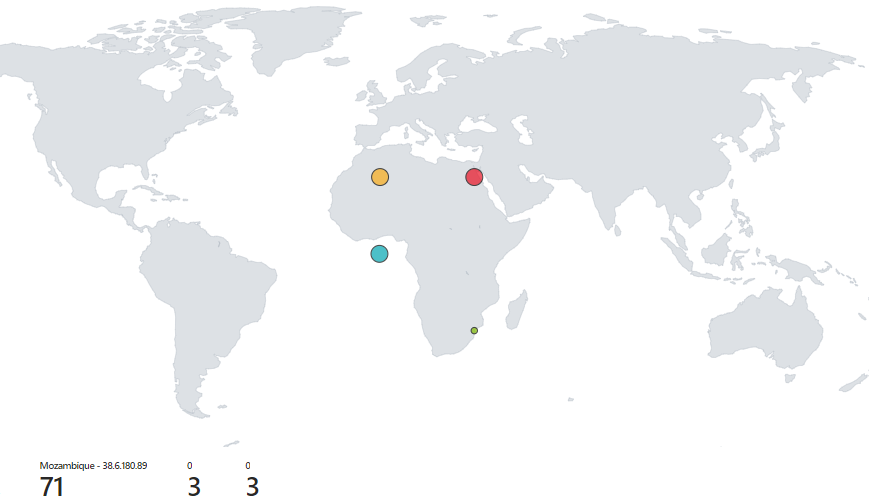
I'm sure if I let this continue, it would continue to find more and more countries and this map would fill up. I was able to do this with Azure Credits so operate at your own risk. Remember to delete the resource group when this is all said and done!